Vulnerability Report Template
Vulnerability Report Template - See also the.docx template and an example of what a basic web form to accept submissions looks like. Perform system and network scanning. The process of hunting weaknesses in a digital system and exploiting the same has jumped significantly, the. Web a new report on vulnerability exploitation has painted a glum picture of cybersecurity. Identify all systems, applications and data to be assessed. Web vulnerability risk assessment template. This report serves as the main method of. Web vulnerability disclosure policy template. The best vulnerability reports provide security teams with all the information needed to verify and validate the issue. Web our vulnerability assessment report template outlines a detailed workflow for identifying, assessing and resolving system and network vulnerabilities effectively. See also the.docx template and an example of what a basic web form to accept submissions looks like. Web sample penetration testing report template 👇. The nessus scan report presents extensive data about vulnerabilities detected on the network. Web vulnerability disclosure policy template. Web vulnerability scanning and reporting are essential steps in evaluating and improving the security of a network. See also the.docx template and an example of what a basic web form to accept submissions looks like. The findings of this assessment are all included in the vulnerability assessment report. Written by experienced security experts. Web the vulnerability assessment report is a part and most crucial step of vulnerability assessment. Web a vulnerability assessment report details the security weaknesses. Web try smartsheet for free. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of those vulnerabilities. Web the vulnerability assessment report is a part and most crucial step of vulnerability assessment. Web vulnerability scanning and reporting are essential steps in evaluating and improving the security of a network. What is. Identify all systems, applications and data to be assessed. Web vulnerability management, new features. Web tenable vulnerability management provides a selection of report templates and customizable report formats. Web the vulnerability assessment report is a part and most crucial step of vulnerability assessment. It is your roadmap to a better state of security preparedness, laying out the unique risks you. The audit was performed on “date” using nessus v8.2.2. Web complete templates of issues, cwe, cve, mitre att&ck, pci dss, aes encryption, nessus burp openvas nmap bugcrowd issues import, jira export, txt/html/pdf report, attachments, automatic changelog and statistics,. The nessus scan report presents extensive data about vulnerabilities detected on the network. Web sample penetration testing report template 👇. See penetration. Written by experienced security experts. Web sample network vulnerability assessment report. Web a vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. What is a penetration testing report? The findings of this assessment are all included in the vulnerability assessment report. Web vulnerability scanning and reporting are essential steps in evaluating and improving the security of a network. The process of hunting weaknesses in a digital system and exploiting the same has jumped significantly, the. Web download our free vulnerability assessment template today! In this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security. Web vulnerability risk assessment template. Identify and outline the scope of the assessment. This means that specific vulnerabilities can be included or excluded in these sections based on. Web the vulnerability assessment report is a part and most crucial step of vulnerability assessment. Perform system and network scanning. Web try smartsheet for free. What is the problem that creates the vulnerability? Web tenable vulnerability management provides a selection of report templates and customizable report formats. By kate eby | february 8, 2023. Web vulnerability risk assessment template. What are the attacks that target this vulnerability? When creating a report, it is necessary to understand the vulnerability assessment process. Some of the following documents report sections can have vulnerability filters applied to them. The nessus scan report presents extensive data about vulnerabilities detected on the network. What are the technical impacts of this vulnerability? Perform system and network scanning. Click here to learn more for a comprehensive list of report templates. Web vulnerability management, new features. Web a vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. Some of the following documents report sections can have vulnerability filters applied to them. It is your roadmap to a better state of security preparedness, laying out the unique risks you face due to the technology that underpins your organization. Web tenable vulnerability management provides a selection of report templates and customizable report formats. The best vulnerability reports provide security teams with all the information needed to verify and validate the issue. Of the 35 hosts identified, 32 systems were found to be active and were scanned. What is the problem that creates the vulnerability? Web vulnerability scanning and reporting are essential steps in evaluating and improving the security of a network. What are the attacks that target this vulnerability? The findings of this assessment are all included in the vulnerability assessment report. The audit was performed on “date” using nessus v8.2.2. See also the.docx template and an example of what a basic web form to accept submissions looks like. Web vulnerability risk assessment template.
Vulnerability Reporting Template

Vulnerability Report Template

Critical and Exploitable Vulnerabilities Report SC Report Template

Vulnerability Management Report Template

Vulnerability Assessment Template Download Printable PDF Templateroller
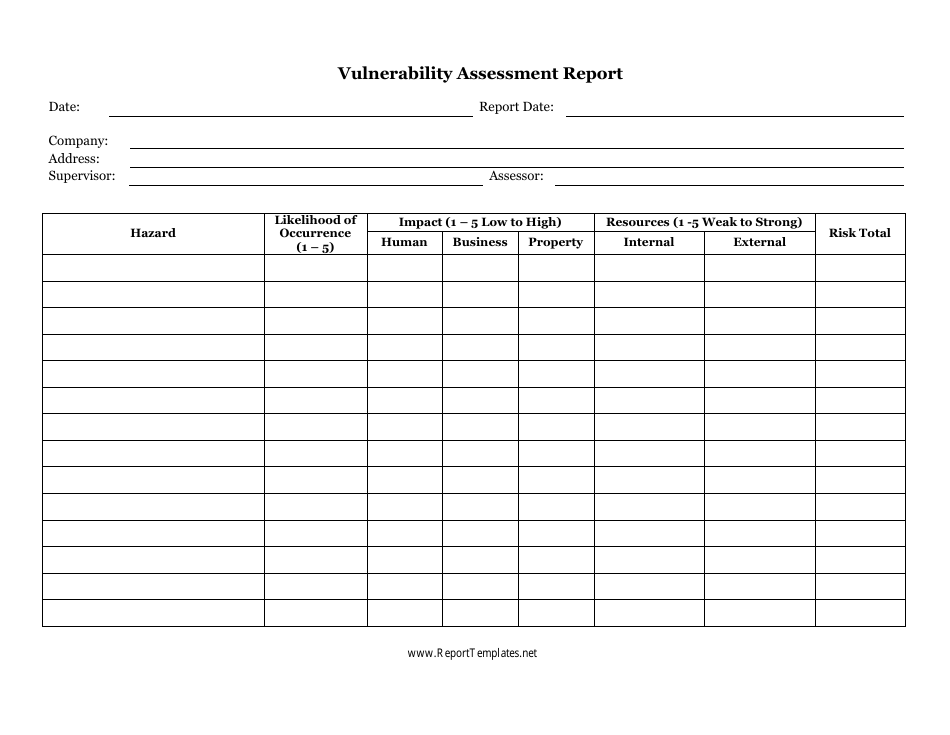
Vulnerability Assessment Report Template Fill Out, Sign Online and
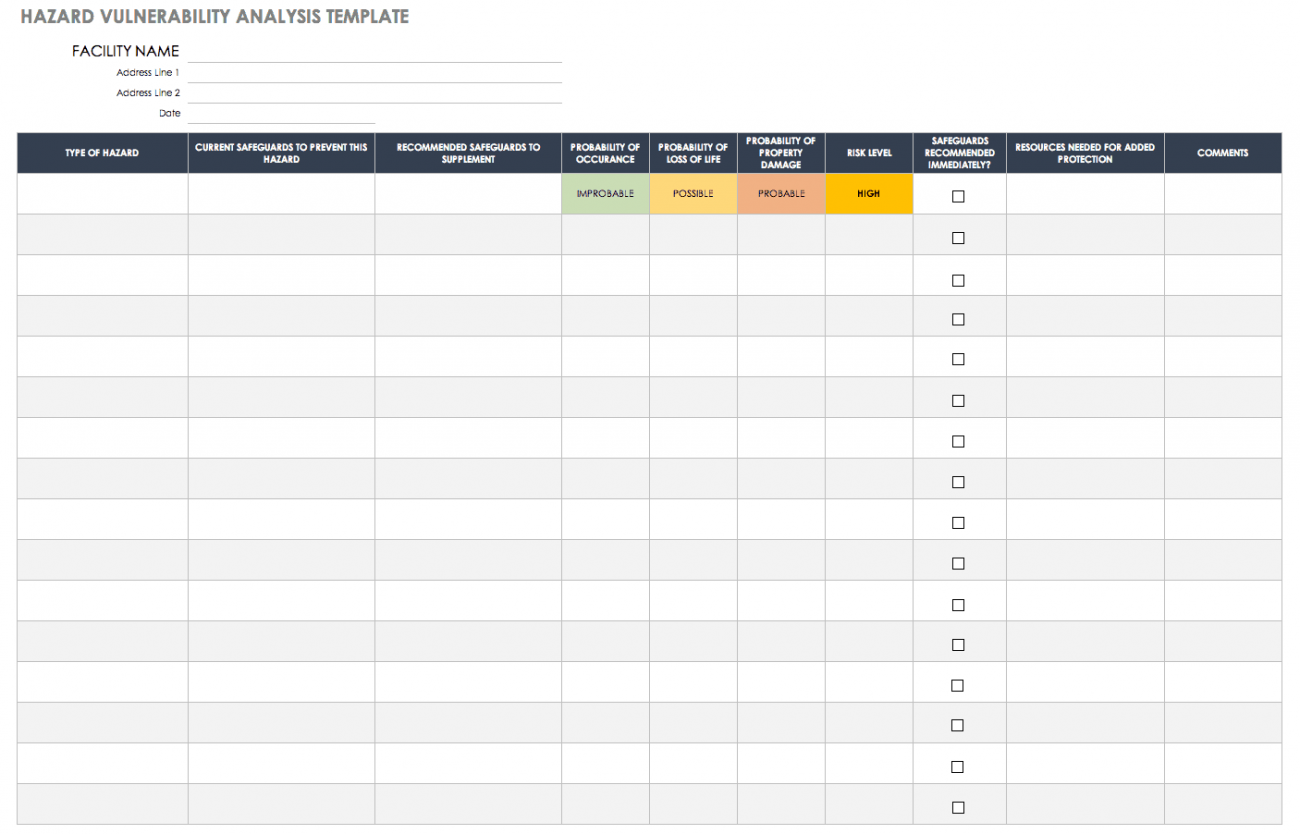
Free Vulnerability Assessment Templates Smartsheet

Vulnerability Report Template
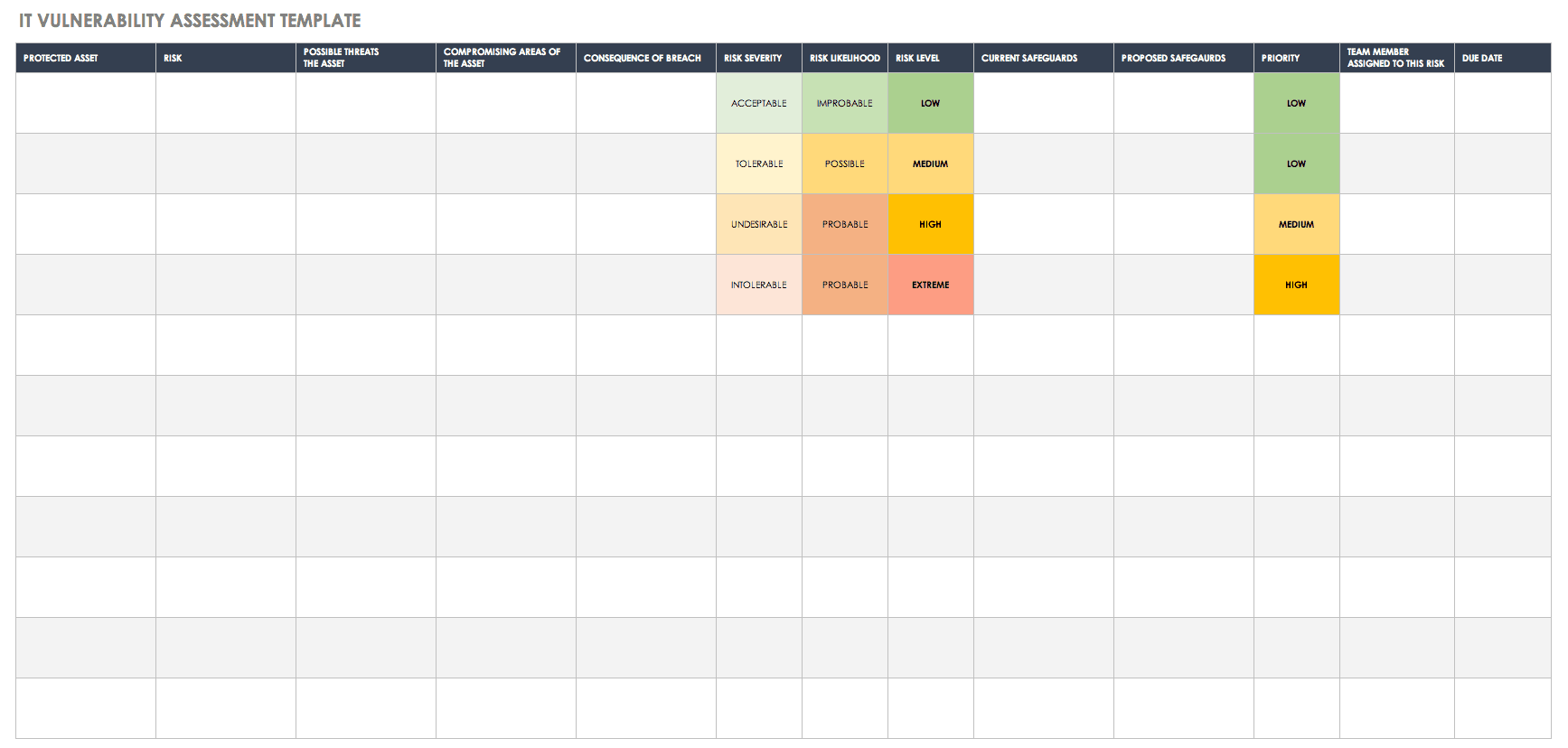
Free Vulnerability Assessment Templates Smartsheet

Free Vulnerability Assessment Templates Smartsheet
Talk About The Factors That Make This Vulnerability Likely Or Unlikely To Actually Happen
Written By Experienced Security Experts.
What Are The Technical Impacts Of This Vulnerability?
Web Creating A Vulnerability Assessment Report Involves Analyzing An Organization’s Systems, Diagnosing System Vulnerabilities, And Describing The Severity Of Those Vulnerabilities.
Related Post: