Gitlab Sast Template
Gitlab Sast Template - The whitepaper a seismic shift in application security explains how 4 of the top 6 attacks were application based. This direction page describes gitlab's plans for the sast category, which checks source code to find possible security vulnerabilities. Web static application security testing (sast) uses analyzers to detect vulnerabilities in source code. $ci_commit_branch == main || $ci_merge_request_target_branch_name == main variables: Manuel grabowski authored 7 months ago. The second job for configuration tags globally for all jobs in template: Web static application security testing (sast) tier: Craig smith authored 1 day ago. The ci/cd template for job definition is supported on gitlab 11.9 and later versions. To run sast jobs, by default, you need gitlab runner with the docker or kubernetes executor. Web select build > pipeline editor. Download it to learn how to protect your organization. Everyone can contribute to where gitlab sast goes next, and we'd love to hear from you. Web static application security testing (sast) (free) all open source (oss) analyzers were moved from gitlab ultimate to gitlab free in gitlab 13.3. Web since gitlab 11.9, a ci/cd. The ci/cd template for job definition is supported on gitlab 11.9 and later versions. Web static application security testing (sast) uses analyzers to detect vulnerabilities in source code. Details of vulnerabilities detected are provided in the merge request. Sast runs in the test stage, which is available by default. '$ci_commit_branch != prod && $ci_commit_branch !=test' note: Web static application security testing (sast) (free) all open source (oss) analyzers were moved from gitlab ultimate to gitlab free in gitlab 13.3. Asked 3 years, 2 months ago. Source code analysis occurs on every code commit. To run sast jobs, by default, you need gitlab runner with the docker or kubernetes executor. There are two kinds of customization: This analyzer scans many languages in a single ci/cd pipeline job. Modified 3 years, 2 months ago. This page is maintained by the product manager for static analysis, connor gilbert. This default configuration will scan your code using a set of rules written by gitlab and r2c that are nearly identical to those previously used by bandit and eslint (. To run sast jobs, by default, you need gitlab runner with the docker or kubernetes executor. All open source (oss) analyzers were moved to gitlab free in gitlab 13.3. Craig smith authored 1 day ago. It seems like you can get away with simply overriding the sast block. The whitepaper a seismic shift in application security explains how 4 of. The whitepaper “a seismic shift in application security” explains how 4 of the top 6 attacks were application based. All open source (oss) analyzers were moved to gitlab free in gitlab 13.3. Static application security testing (sast) (free) introduced in gitlab ultimate 10.3. There are two kinds of customization: The whitepaper a seismic shift in application security explains how 4. Upgrade sast and iac analyzer to v5. The whitepaper a seismic shift in application security explains how 4 of the top 6 attacks were application based. $ci_commit_branch == main || $ci_merge_request_target_branch_name == main variables: For building a complete custom configuration, we rely on a passthrough chain. This section describes how to use it and customize its execution. The whitepaper “a seismic shift in application security” explains how 4 of the top 6 attacks were application based. Craig smith authored 1 day ago. Web since gitlab 11.9, a ci/cd template with the default sast job definition is provided as a part of your gitlab installation. The second job for configuration tags globally for all jobs in template: Details. Web static application security testing (sast) uses analyzers to detect vulnerabilities in source code. This default configuration will scan your code using a set of rules written by gitlab and r2c that are nearly identical to those previously used by bandit and eslint ( see the rules here ). There are two kinds of customization: Web static application security testing. If an include line already exists, add only the template line below it. The whitepaper a seismic shift in application security explains how 4 of the top 6 attacks were application based. Introduction and how you can help. Modified 3 years, 2 months ago. This version brings many exciting improvements to gitlab, but also removes some deprecated features. Modifying the behavior of predefined rules. Assign users and groups as approvers for specific file changes. $ci_commit_branch == main || $ci_merge_request_target_branch_name == main variables: Download it to learn how to protect your organization. Static application security testing (sast) (free) introduced in gitlab ultimate 10.3. '$ci_commit_branch != prod && $ci_commit_branch !=test' note: Your parameters need to be updated. A source code analysis can: The 17.0 major release is coming on may 16, 2024! Source code analysis occurs on every code commit. Web static application security testing (sast) (free) all open source (oss) analyzers were moved from gitlab ultimate to gitlab free in gitlab 13.3. Rules is optional, depend on your needs. Web select build > pipeline editor. While using the template, you might experience a job failure or other pipeline error. The whitepaper a seismic shift in application security explains how 4 of the top 6 attacks were application based. You can think of a passthrough as a single step that modifies the custom configuration.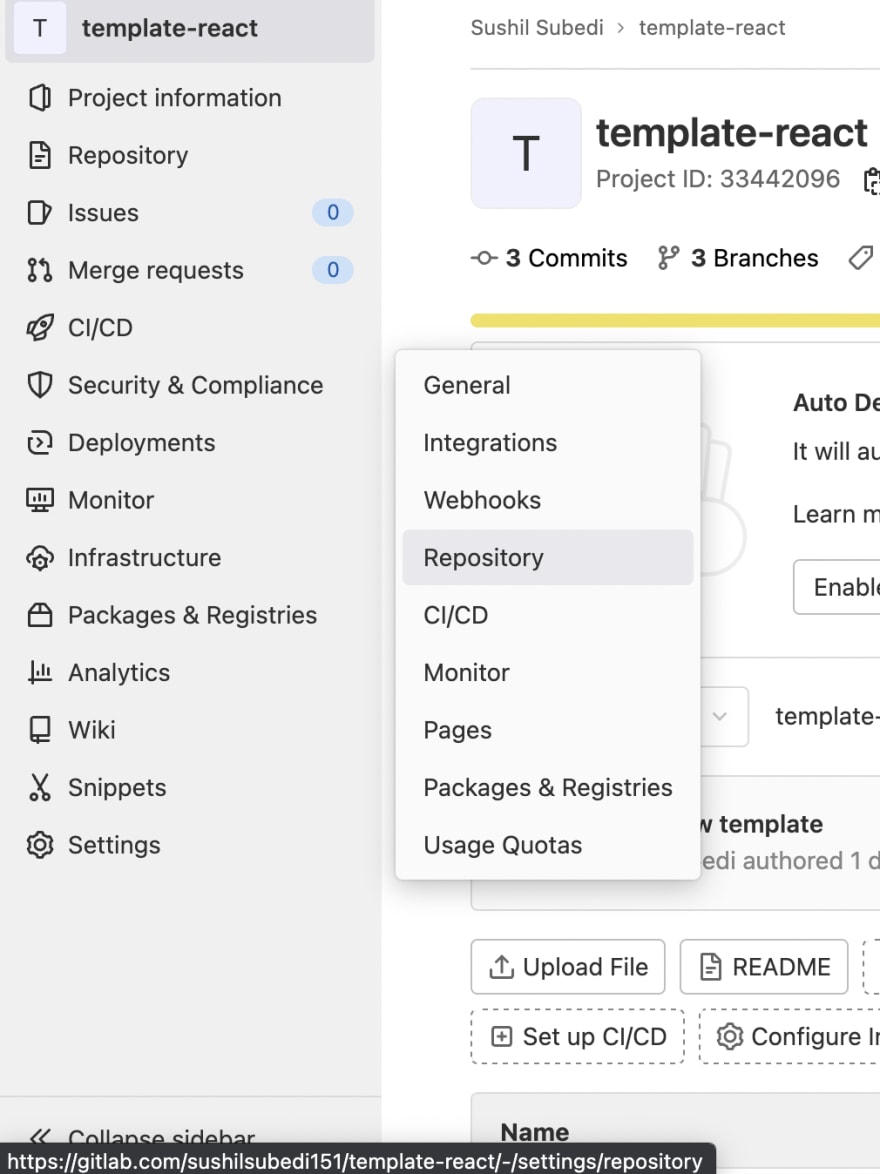
How To Create GitLab Pull Request Template? The Dev Post

Semgrep for GitLab GitLab SAST and Semgrep CI
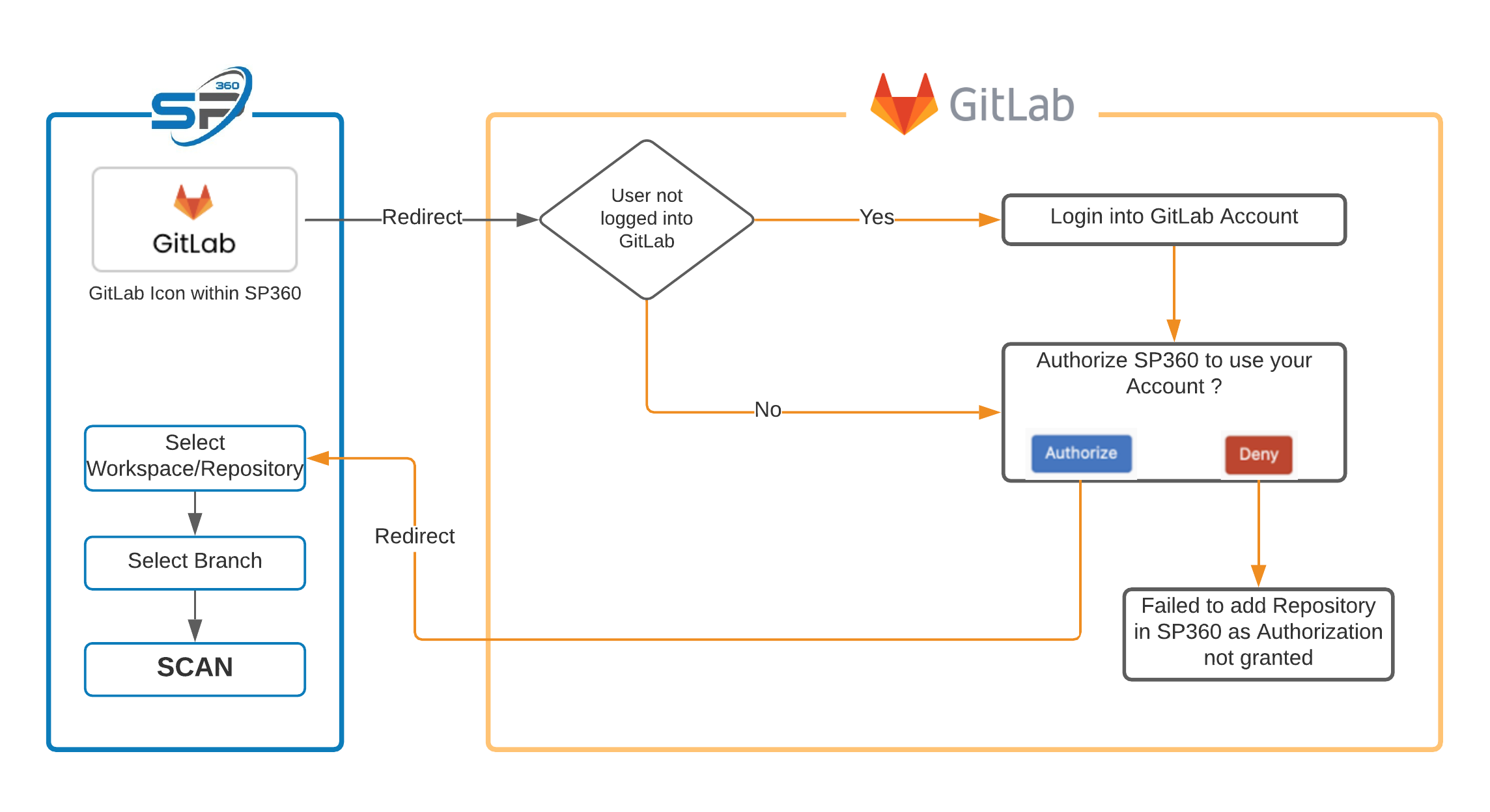
Sast gitlab SP360

GitLab SAST How to Use GitLab With Klocwork Perforce
Gitlab SAST pipline + compliance EXPLAINED YouTube

GitLab SAST Customize Rulesets Demo YouTube

GitLab SAST How to Use GitLab With Klocwork Perforce

Integrating Fortify SAST into a GitLab CI/CD Pipeline YouTube
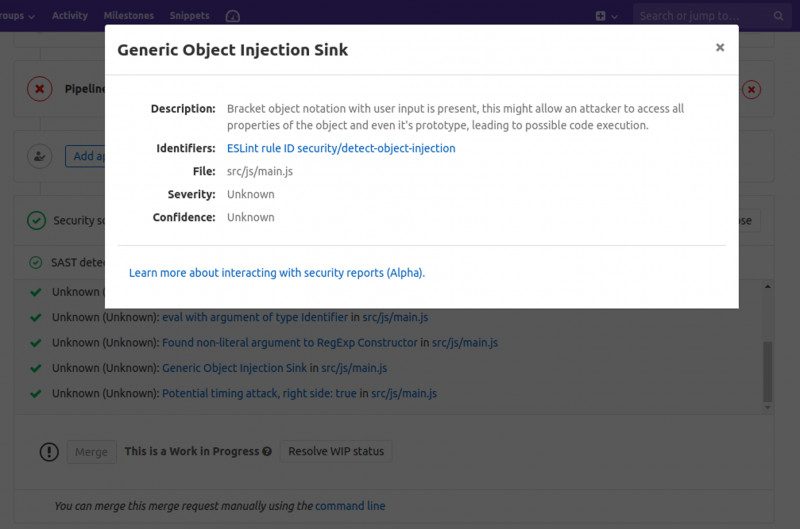
Software Development Status Report Template New Gitlab 11 8 Released

Secure your project with the GitLab SAST analyzers cylab.be
The Whitepaper A Seismic Shift In Application Security Explains How 4 Of The Top 6 Attacks Were Application Based.
This Section Describes How To Use It And Customize Its Execution.
Web Static Application Security Testing (Sast) Tier:
Upgrade Sast And Iac Analyzer To V5.
Related Post: